CyberCrypt
Orchestrating decryption in distributed Environments
Law enforcement agencies increasingly encounter encrypted digital assets in their investigations. Our project was focusing on providing a solution for this challenge by enabling the orchestration of crypto cracking operations in distributed environments.
Project Genesis and Partnership
The need for more effective cryptoanalysis tools led to the launch of the Cybercrypt@gov project, which aimed to develop a scalable, distributed, and high-performance system supporting law enforcement in decrypting secured data.
Recognizing the complexity of the problem, Redge Technologies (formerly Atende Software) was a part of a consortium with leading academic and industrial partners: AGH University of Krakow (consortium leader), Warsaw University of Technology, War Studies University, and Longevity. The project was co-financed by Poland's National Centre for Research and Development (NCBiR) under the Defense and Security Program – Competition No. 9/2018 (Contract No. DOB-BIO9/32/03/2018). The project spanned 2019–2024, with a total budget of 14 534 042 PLN and co-financing amounting to 14 201 042 PLN.
Technical Objectives and System Architecture
The Cybercrypt@gov system was designed from the ground up to provide:
- Distributed task processing across hybrid compute environments (CPU/GPU/FPGA)
- Orchestration of brute-force attacks with existing open-source components
- An intuitive interface for use by non-specialist personnel
- Integrated data extraction tools to prepare encrypted data for analysis
Custom Orchestrator for Hashcat
Hashcat was selected as the foundational engine due to its active development, broad format support, and ability to run on both OpenCL and CUDA. However, existing orchestrators did not meet the consortium’s needs, especially the integration of FPGA-based computations, efficient job scheduling, load balancing, and multi-platform agent coordination.
As a result, the team developed a custom orchestration layer from scratch, enabling:
- Automatic distribution and synchronization of computational tasks
- Unified control of heterogeneous compute nodes (CPU, GPU, FPGA)
- Real-time progress tracking and task management
Extraction Tool – Preparing Data for Decryption
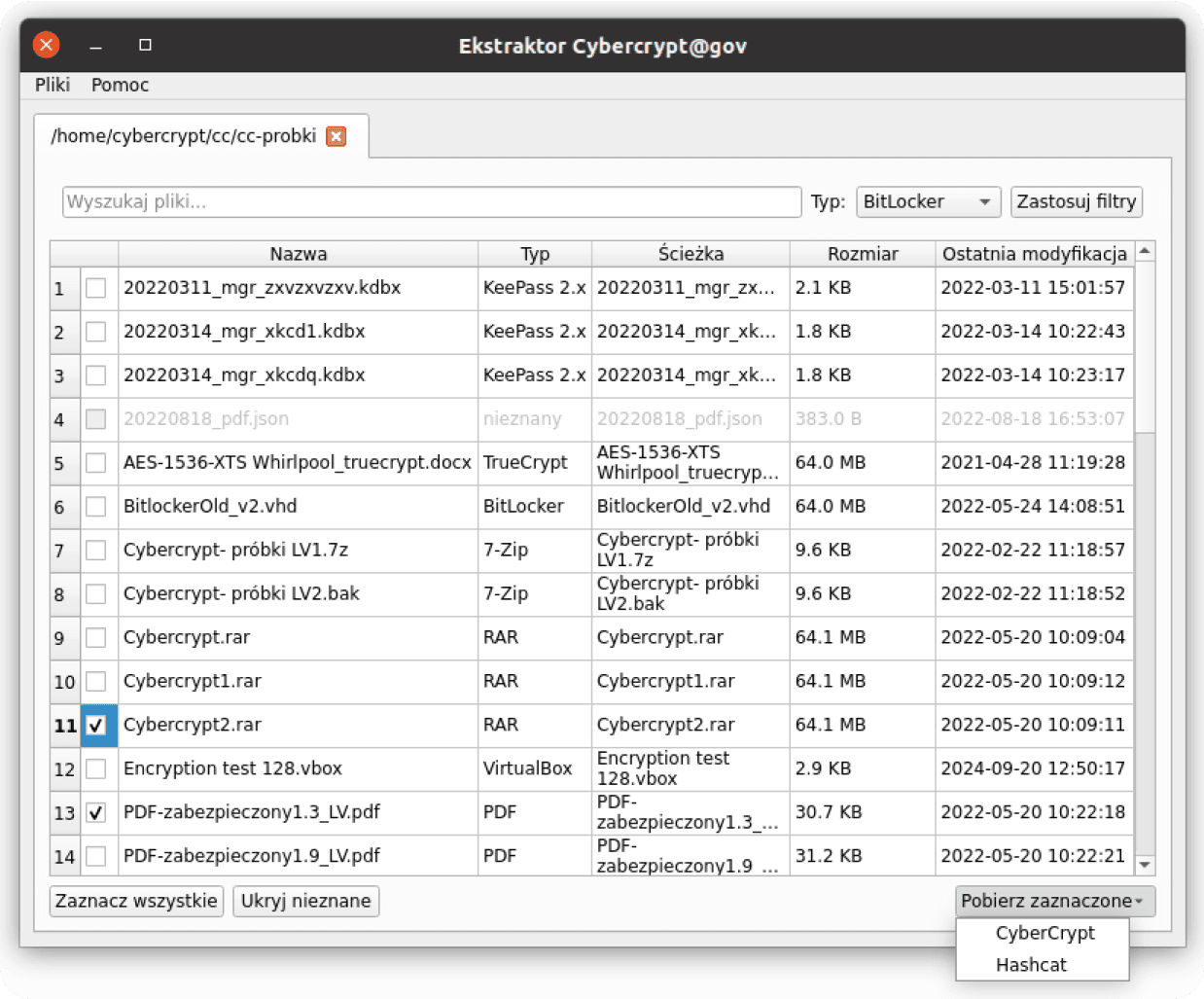
A critical component of the system is a dedicated Extraction Tool, developed to streamline the preparation of encrypted materials. Unlike fragmented or script-based solutions, this tool:
- Automatically detects encrypted files and volumes across user-defined directories, individual files, and connected storage devices
- Recognizes file types based on content rather than name or extension
- Requires no expert knowledge to extract cryptographic material
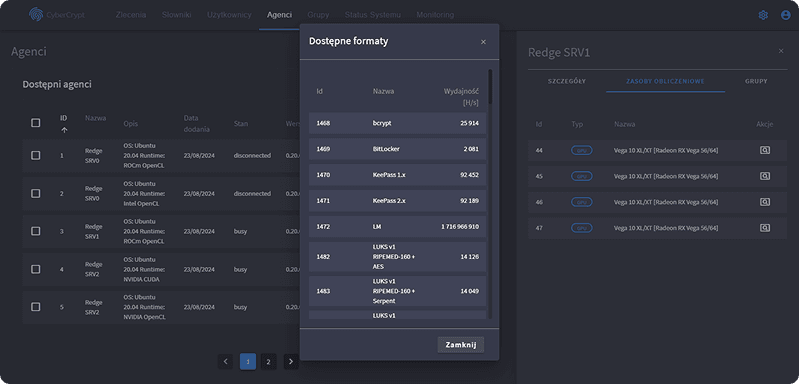
- Supports output in Cybercrypt (project-native) and Hashcat formats
Supported formats include:
- Archives: 7-Zip, RAR, WinZip
- Password managers: KeePass (1.x and 2.x)
- Documents: MS Office, PDF
- Disks/volumes: TrueCrypt, VeraCrypt, BitLocker, LUKS, VirtualBox
- Key files: PEM (PKCS#8)

Administrative Console (Panel)
The system’s Administrative Panel allows users to:
- Upload multiple extraction results
- Input custom hash values (18 supported functions)
- Select dictionaries/masks for attacks
- Prioritize and schedule jobs
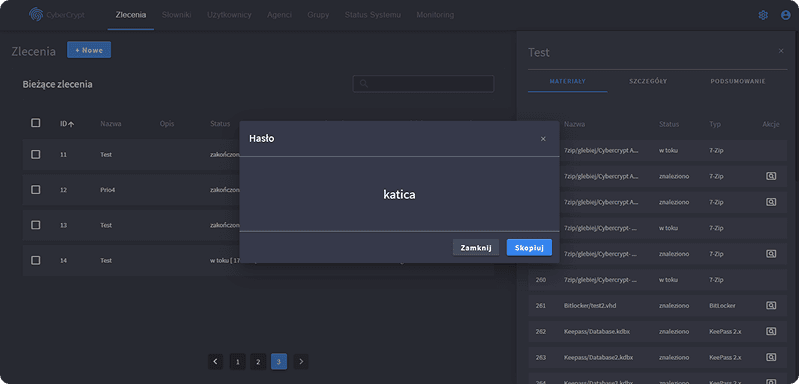
- Monitor ongoing tasks and access real-time results
Partial results (recovered passwords) are made available immediately, even before a task finishes. The console also enables:
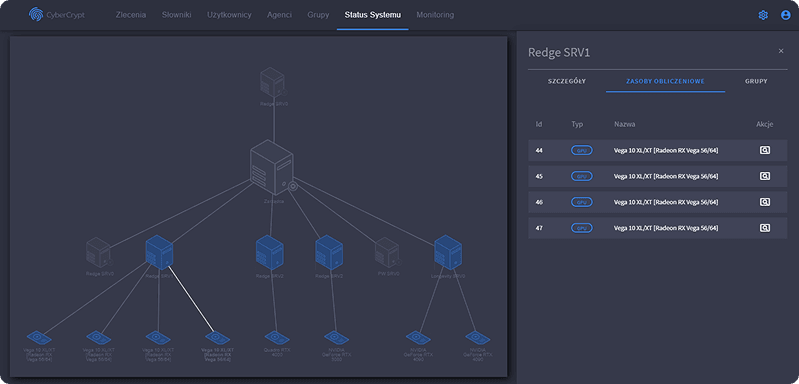
- Resource grouping for workload segmentation
- Full system monitoring (status of agents, resource usage)
- User and permission management
- Centralized dictionary management
Hardware Platform Evaluation
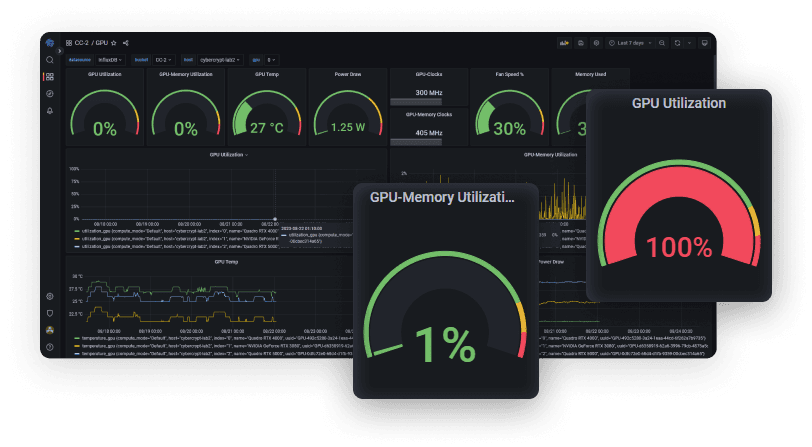
The project involved intensive benchmarking across a range of compute platforms:
- CPU: Intel and AMD architectures
- GPU: Consumer and professional-grade NVIDIA and AMD GPUs
- FPGA: Custom-designed accelerators developed by Warsaw University of Technology, based on Xilinx chips
This evaluation informed optimal deployment configurations and demonstrated the feasibility of hybrid CPU/GPU/FPGA operations within the same framework.

Outcomes and Impact

The result of the Cybercrypt@gov project is a functional system at Technology Readiness Level 8 (TRL 8) — fully tested and demonstrated. It has been deployed operationally at Polish National Police significantly enhancing their ability to tackle encrypted evidence in criminal investigations.
The system’s scalable architecture supports virtually unlimited compute expansion — any number of nodes can be connected, making it adaptable to the available hardware. Its modular design and intuitive interface enable non-technical users to execute highly technical operations with minimal training.
Cybercrypt@gov showcases the intersection of academic innovation, industry-grade engineering, and practical national security needs. Redge Technologies’ contribution — from system design to software development and integration — was critical to delivering a robust, real-world solution.
This project highlights how purpose-built tools, designed with real operational constraints in mind, can provide a competitive edge against increasingly sophisticated cybercriminals.

Contact us
We can adjust the technology to your needs. Hence, we listen carefully how we can help.
Contact us